Antivirus is one of the first things most people install on a new PC. After all, nobody wants malware ruining their PC or, worse, stealing their data. And to be fair, most popular antivirus suites do a decent job of protecting your PC. But the problem is, they aren’t exactly optimized to be lean or lightweight. And things have become even worse ever since antivirus suites have started bundling extras like VPNs, parental controls, and browser add-ons.
All of this leaves the apps and games you actually use with fewer resources, which causes frequent slowdowns and even lag. So the uncomfortable irony is that the software meant to protect your PC ends up being the very thing holding it back.
How antivirus software can slow down your PC
When constant protection becomes constant pressure
Antivirus softwares love to present themselves as silent protectors. Always watching, always keeping you safe, and never getting in your way. Sure enough, part of this is true. They work in the background, but it’s not without any impact.
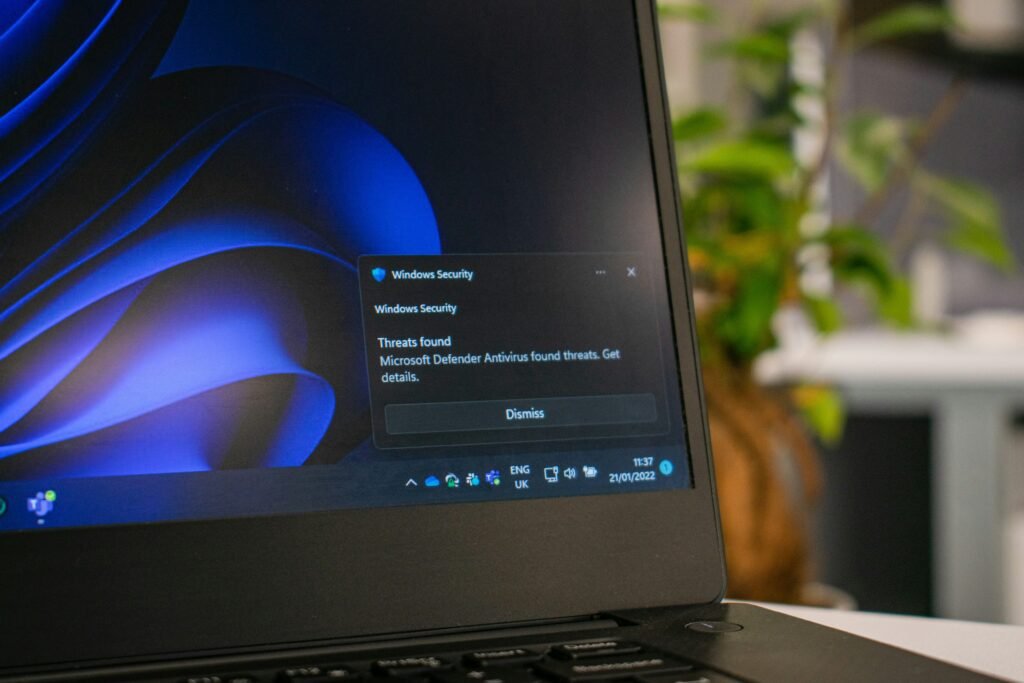
Antivirus programs work by scanning files as they are opened, downloaded, copied, or modified. That means every app you launch and every document you touch triggers a quick inspection. There are also the scheduled scans, which often run when you least expect them. So if your PC has ever felt slow, even when you’ve got nothing running, it’s probably the antivirus program combing through your files in the background.
Now, the performance hit isn’t the same every time. During light, routine scans, the impact can be minimal, anywhere from 0 to 20 percent. However, during full or partial scans, this can rise up to as high as 50 percent. The impact also varies depending on the antivirus program you’re using. Some are lightweight and efficient, while others are far more demanding.
Most of the time, you may not even notice this slowdown. But as soon as you start gaming, editing videos, or running any resource-intensive apps, the story will change. That’s when both your app or game and antivirus program start to compete for the same system resources, and the performance takes a hit.
To make matters worse, modern antivirus rarely sticks to just antivirus duties. Most of them come bundled with all sorts of extras, like VPNs, password managers, and system optimizers. All of these extras run separate processes. So yes, it’s not just one program you’re dealing with. Your PC is actually running multiple different software under a single name.
You can verify if the antivirus is the bottleneck
Be sure before you act
!–>