G Data Antivirus
Most big-name antivirus companies like to boast about their years of experience, but few can match G Data in this respect. Not only has the German developer been around for more than 30 years, it also claims to have developed the first antivirus program way back in 1985.
Fast forward to today and G Data has highly-rated consumer security products for Windows, Android and Mac, as well as some very comprehensive endpoint solutions for businesses.
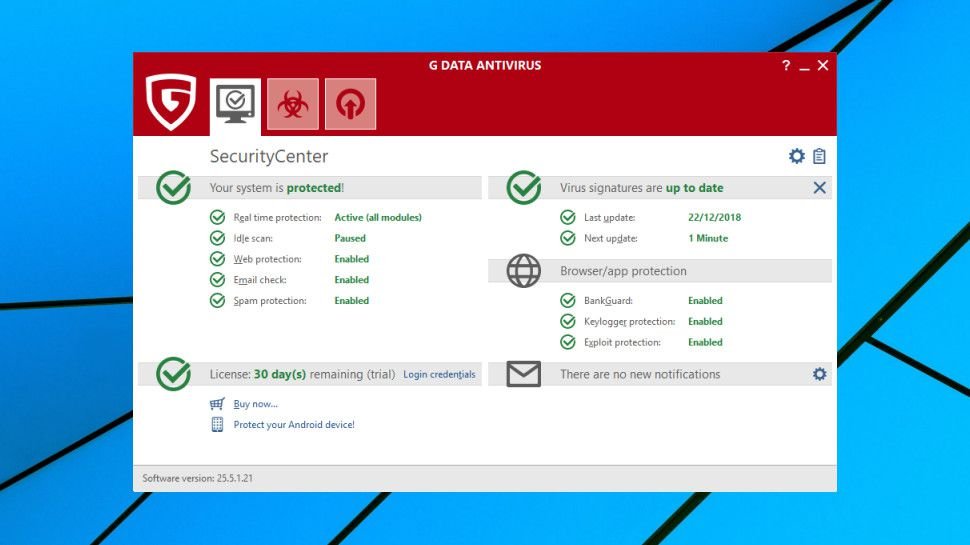
The range starts with G Data Antivirus which we are reviewing here. Despite being the baseline product, it goes beyond the usual PC antivirus fundamentals, with exploit protection, anti-ransomware, URL filtering, a spam filter, and specialist browser hardening to help secure online banking and shopping.
- You can sign up for G Data Antivirus here
The program uses multiple technologies to keep you safe, including its own engine, the Bitdefender engine, and a CYREN-based layer to better detect outbreaks as they happen.
Single device licenses are top of the normal range at £30 ($39) for a year. Top packages like Bitdefender Antivirus Plus are the same price, but many come in cheaper, and for example Kaspersky Anti-Virus costs £25 ($32.50) to cover one device for a year.
There are savings available if you’re adding computers or extending the license term, so for example a five PC, two-year license costs only £95 ($123.50). But other vendors do much the same, and covering those devices with Kaspersky Anti-Virus would cost just £80 ($104).
A free trial is available, and there’s the added security of a 30-day money-back guarantee if you run into problems.
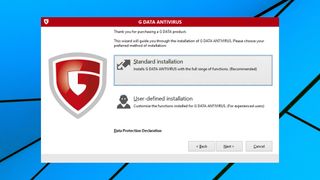
Setup
The G Data Antivirus trial was simple to find and download. The installer took a while to download the setup components it needs, but after that everything ran smoothly, with no hassles or complications.
As with many competitors, G Data asks you to register the program by providing your name and email address. The installer also asks for your physical address and phone number, but providing them is optional, and we were able to leave those boxes blank.
Moments after the main setup process was complete, a pop-up window recommended we install G Data WebProtection, a Chrome extension which prevents you accessing phishing, scam and malicious sites. We would much prefer this to be handled at the network level to ensure it covers all browsers and applications, but G Data claims this improves accuracy (we’re unsure how).
Rebooting, we found G Data had added 600MB of code to our hard drive and no less than seven new background processes. They typically consumed a minimal 250MB, but when our system was under load, it did seem to be noticeably slower than usual. We didn’t try to come up with an objective measurement of G
Be the first to write a comment.