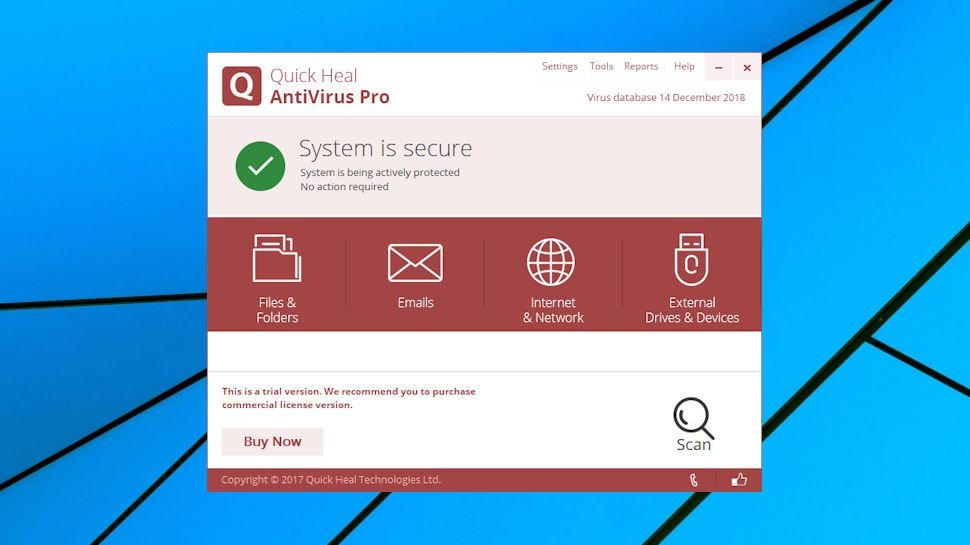
Quick Heal AntiVirus Pro
Quick Heal Technologies is an Indian company which develops security and antivirus software under its own name, and produces enterprise offerings under the Seqrite brand.
Quick Heal AntiVirus Pro is the company’s starter product for home users, although you wouldn’t know that from the feature list. It has a firewall, sandbox, anti-keylogger, intrusion detection, along with a ‘TrackMyLaptop’ antitheft system: it seems more like a suite than a standalone antivirus.
The program works on anything from Windows 2000 up, which is unusual when much of the competition now requires Windows 7 or later. (Although, of course, if you’re still using the long-unsupported Windows 2000 or XP, you’re got way more security problems to worry about than your choice of antivirus).
- You can sign up for Quick Heal AntiVirus Pro here
Quick Heal AntiVirus Pro is priced at $30 (£23.08) for a one-year, one-device license. There’s a discount for adding more devices, but it’s relatively poor, with a three-device license costing $75 (£57.70), and five devices $125 (£96.15).
By comparison, the excellent Bitdefender Antivirus Plus is more expensive for a single device, at £30 ($39) a year. But you can cover five devices for only £50 ($65), and 10 devices for £55 ($71.50).
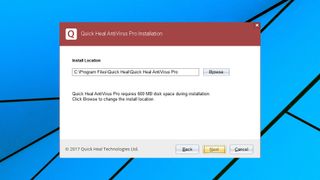
Setup
The Quick Heal AntiVirus Pro 30-day trial build was easy to find on the website, but getting it set up took more effort than we expected. We launched the installer, it displayed a couple of windows for a tiny fraction of a second, they disappeared before we could read them, and – that was it. There were no error messages, no logs or anything else to give us a clue about the cause.
Seeing an opportunity to test support, we raised a ticket explaining the problem, saying that our Windows 10 system had no other antivirus installed and we’d even disabled Windows Defender, with no change.
We hoped to get a detailed reply with Quick Heal-specific information. We would have accepted a page of generic advice (clear temporary folders, close other running apps, download and run the installer again). What we actually got, some 15 hours later, was the following:
‘Well, not only do you need to turn Windows Defender OFF, but also totally uninstall it.’
As troubleshooting advice goes, this was worse than useless, as there’s no way to ‘totally uninstall’ Windows Defender in Windows 10. Users who didn’t have the experience to dismiss this as nonsense might easily waste time messing around with their system, maybe even causing other problems, trying to do what the agent had asked.
With no effective help on offer, we switched to our emergency fallback position of installing to a fresh user account. Setup proceeded without any further hassles,
Be the first to write a comment.