K7 Antivirus Premium
K7 Computing may not have the profile of the big-name competition, but there’s more to the Indian company than you might think: 25+ years of antivirus experience, VirusTotal and OPSWAT partners, a range of home and business products, and more than 20 million users around the world.
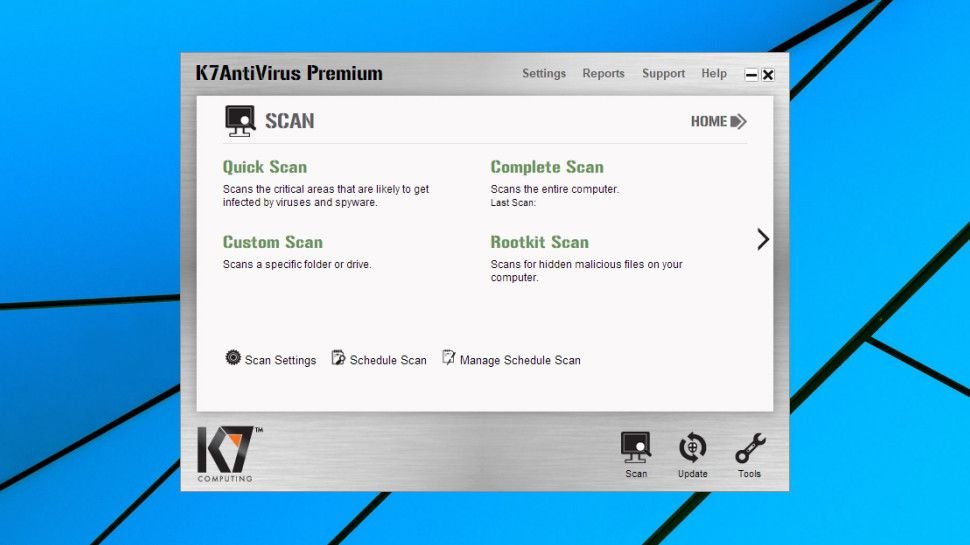
K7 Antivirus Premium is the starter product in the range, but don’t assume that means it’s short on features. There’s antivirus, exploit protection, a firewall, device control, USB vaccination, basic system clean-up tools and a virtual keyboard.
- You can sign up for K7 Antivirus Premium here
There’s also a notable omission, though, in the lack of any URL filtering. Many antivirus packages will try to detect and block access to malicious or phishing websites, but not this one.
Single user pricing is good, with the package costing a mere $25 for a one device, one-year license. Kaspersky Anti-Virus doesn’t have all the functionality of K7 Antivirus Premium, but it’s noticeably more expensive at $32.50 (£25).
Add users and years and it’s a little different. A five device, two-year license for K7 Antivirus Premium is $100; an equivalent Kaspersky license is a near identical $104 (£80). K7 still looks like good value for the features you get, but the price advantages fade if you opt for a multi-user license.
If you’re intrigued by the lengthy feature list and low price, a free 30-day trial gives you a risk-free way to find out more.

Setup
The K7 Antivirus Premium installer looked very simple, just a ‘View EULA’ link and an ‘Install’ button, with not as much as a ‘choose your installation folder’ option to get in the way. So, we tapped Install and watched as the setup window disappeared, and – didn’t return. No ‘Done’ message, no ‘Please reboot’ advice, nothing at all.
Task Manager didn’t show any running installer, but the process didn’t seem to have finished properly, either (there was no K7 shortcut on our desktop, nothing on the Start menu, no K7 icon in our system tray.)
We rebooted, and a K7 icon appeared in our system tray. Unfortunately, it wouldn’t respond to our left or right-clicks, just displaying a tooltip of ‘Activation Pending.’ After a few minutes, pop-ups asked us if we wanted to activate and update the package, but when we clicked ‘yes please’, warned us that the update had failed, and we should reinstall.
While this sounds easy, it really wasn’t. Just as had happened in our last K7 review (though for different reasons), our first installation was broken. When we ran the installer again, it told us K7 Antivirus Premium was installed already and we should uninstall it; when we tried to run the uninstaller, it told us the process had failed and we should reinstall. Deadlock.
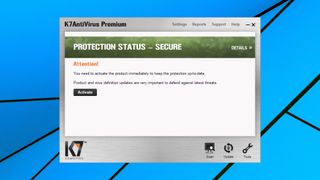
We went to work, finding and running K7’s cleanup tool ourselves, cleaning our temporary folders, rebooting, closing all non-essential apps, trying K7’s installer again, and – this time, we appeared to be in
Be the first to write a comment.