We found a massive spam operation — and sunk its server

For ten daysin March, millions were caught in the same massive spam campaign.
Each email looked like it came from someone the recipient knew: the spammer took stolen email addresses and passwords, quietly logged into their email account, scraped their recently sent emails and pushed out personalized emails to the recipient of that sent email with a link to a fake site pushing a weight loss pill or a bitcoin scam.
The emails were so convincing more than 100,000 people clicked through.
We know this because a security researcher found the server leaking the entire operation. The spammer had forgotten to set a password.
Security researcher Bob Diachenko found the leaking data and with help from TechCrunch analyzed the server. At the time of the discovery, the spammer’s rig was no longer running. It had done its job, and the spammer had likely moved onto another server — likely in an effort to avoid getting blacklisted by anti-spam providers. But the server was primed to start spamming again.
Given there were more than three million unique exposed credentials sitting on this spammer’s server — hosted onintelimost.com, we wanted to secure the data as soon as possible. With no contact information for the spammer — surprise, surprise — we asked the hosting provider, Awknet, to pull the server offline. Within a few hours of making contact, the provider nullrouted the server, forcing all its network traffic into a sinkhole.
TechCrunch provided a copy of the database to Troy Hunt. Anyone can now check breach notification site Have I Been Pwned to see if their email was misused.
But the dormant server — while it was still active — offered a rare opportunity to understand how a spam operation works.
The one thing we didn’t have was the spam email itself. We reached out to dozens of people to ask about the email they received. Two replied — but only one still had a copy of the email.
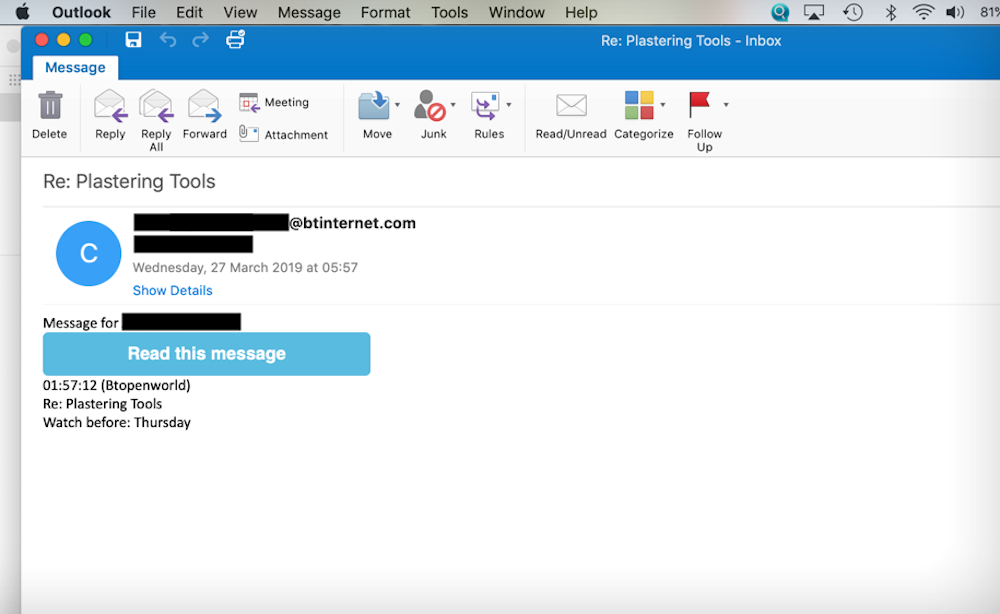
The email sent by the spammer. (Image: supplied)
“The same mail appeared on three occasions,” said one of the recipients in an email to TechCrunch. “The subject was related to an email I had sent previously
Be the first to write a comment.



